Samsung Galaxy A12 FRP Bypass (Android 12/13, 2026): Why No-PC Methods Fail & The Verified MTK Solution
Quick Summary: Key Takeaways
- The “No PC” Reality: On Android 12 and 13 (Security Patch Level 2024/2025), manual “No PC” methods like TalkBack or SIM PIN have a success rate of less than 10%. Samsung has patched the “Accessibility” and “Knox” loopholes these exploits require.
- Chipset Specifics: The standard Galaxy A12 (SM-A125F) runs on a MediaTek Helio P35 chipset. It requires different drivers and tools than the A12 Nacho (Exynos), which shares the same body but different internal architecture.
- Safest Solution: The most reliable method is using the SamFw FRP Tool (or similar MTK-client) which automates the “Auth Bypass” and interacts directly with the hardware partition.
- Critical Driver Step: Windows 10 and 11 users must disable “Driver Signature Enforcement” to install the necessary MediaTek Preloader drivers, or the connection will fail.
Facing a locked device when you need it most creates immediate stress. I recently encountered this firsthand when I bought a used Galaxy A12 for my teenager. After performing a factory reset, the phone demanded the previous owner’s credentials, effectively rendering the device unusable. Like many users, I immediately searched for a Samsung A12 FRP bypass without PC or SIM, hoping for a manual fix to get past the “Verify your account” screen.
However, the reality of bypassing Google account verification in 2026 is complex. While video platforms host thousands of tutorials showing manual exploits, many rely on outdated software vulnerabilities that Samsung has long since patched. To ensure you do not spend hours attempting methods that no longer exist, this guide documents exactly why A12 FRP no SIM method attempts fail on modern firmware and provides the confirmed, working solution for the MediaTek Helio P35 MT6765 chipset found in this device.
Decision Guide: Manual Exploits vs. MediaTek Solutions
Selecting the correct bypass method depends entirely on your device’s current Android version and security patch level. While a Samsung A12 FRP bypass without PC or SIM is the ideal scenario for most users, the success rate of manual methods has dropped significantly on devices running Android 12.
During my analysis of the test device, I found that the time invested in manual exploits often failed. The Samsung Setup Wizard has been fortified against the glitches that previously allowed access to the browser. In contrast, PC-assisted methods targeting the MediaTek Helio P35 MT6765 chipset were nearly instant because they communicate with the phone before the Android operating system fully boots.
Method Comparison: What Still Works in 2026?
The following table outlines the current state of bypass techniques for the SM-A125F as of 2026:
| Method | Success Rate (Android 12/13) | Time Required | Complexity | Sustainability |
| TalkBack / Accessibility | < 10% (Highly Patched) | 45+ Minutes | High (Many steps) | Low (Patched frequently) |
| SIM PIN Exploit | < 15% | 30 Minutes | Medium | Low (Depends on timing) |
| PC-Assisted MTK Tool | > 95% | 5-10 Minutes | Low (Automated) | High (Hardware-level) |
Why ‘No PC’ Methods (TalkBack & SIM PIN) Fail on Android 12
Short answer: On Samsung Galaxy A12 devices running Android 12 or 13, no-PC FRP bypass methods no longer work reliably due to patched Samsung Knox and Accessibility exploits.
Many users notice that steps shown in older tutorials simply don’t match what appears on their screen. That’s not user error—it’s the result of firmware-level changes.
The Technical Reason for Failure
The core issue lies in how updated security patch protocols handle the com.android.settings access points.
- Closed Backdoors: Previously, users could exploit the “Emergency Call” dialer or the “Accessibility” menu to inject commands that would force a Chrome browser window to open.
- Patched Menus: On the MediaTek A12, these entry points have been systematically closed. Specifically, the “Help & Feedback” option—which was a primary gateway to opening YouTube and then Chrome—is now hidden or unclickable during the setup phase.
If your device lacks the options shown in a video, it confirms you’re on a secure firmware version where no-PC methods are deprecated.
The Verified Solution: PC-Assisted MTK Bypass (SamFw Tool)
Since the “No PC” avenues are likely patched for your device, the most reliable approach is using a standard utility to handle the MediaTek chipset. Unlike generic methods, this solution uses a specific exploit known as MTK Auth Bypass to communicate with the device’s hardware partition (BROM mode), resetting the protection flag without needing to touch the Android interface.
We recommend the SamFw FRP Tool (Free Version 4.9 or later) for this process. It is a reputable “All-in-One” utility that bundles the necessary scatter files and authentication scripts, removing the need for you to hunt for dangerous raw firmware files or manage complex SP Flash Tool configurations manually.
Prerequisites (Do Not Skip)
- A Windows Computer: Windows 10 or 11 is preferred.
- A USB Data Cable: Original Samsung cables are preferred to avoid connection drops.
- The Software: Download the latest version of SamFw FRP Tool.
- Critical Windows Setting: You must disable “Driver Signature Enforcement.”
Step 1: The “Driver Signature” Obstacle (Crucial)
Before installing any drivers, you must address a Windows security feature that blocks the specialized drivers needed for the A12. The MediaTek Preloader driver is often unsigned, meaning Windows will silently block it, causing your phone to connect and disconnect rapidly.
How to Disable Driver Signature Enforcement:
- Click Start > Settings > Update & Security > Recovery.
- Under Advanced startup, click Restart now.
- Once the PC restarts to a blue menu, select Troubleshoot > Advanced options > Startup Settings > Restart.
- When the PC reboots again, press 7 or F7 on your keyboard to select “Disable driver signature enforcement.”
- Your PC will boot normally. You can now install the Samsung USB Drivers and MediaTek (MTK) USB Drivers.
Step 2: Prepare the Tool
- Open the SamFw Tool as an Administrator.
- Navigate to the MediaTek tab (sometimes labeled “MTK”).
- Unlike older tools where you need to load a specific “Scatter File” manually, this tool detects the chipset automatically. However, ensure “Samsung” is selected in the brand dropdown if available.
- Locate the button labeled “Remove FRP” (or “Factory Reset Protection”).

Professional tool for an S24+ Google account verification bypass
Step 3: Enter BROM Mode (The Connection)
This is the most sensitive part of the process. You are putting the phone into “Boot Read-Only Memory” (BROM) mode, which bypasses the standard bootloader.
- Power off the Samsung A12 completely.
- Wait 10–15 seconds to ensure the logic board is fully powered down.
- In the software on your PC, click “Start” or “Remove FRP” first. The tool will say “Waiting for device…” or “Waiting for USB Port…”
- On the phone: Hold both the Volume Up and Volume Down buttons simultaneously.
- While holding the buttons, connect the USB cable to the phone. Do not press the Power button.
Step 4: Verify Connection and Execution
If your drivers are correct, the tool will detect the device immediately. You should see a log appearing on the screen.
- What you should see: The tool will run a step called “Disable Auth” or “Auth Bypass.” This unlocks the secure boot port.
- Visual Confirmation: If you open Windows Device Manager, under “Ports (COM & LPT),” you should briefly see “MediaTek Preloader USB VCOM (Android)”. If you see “Unknown Device” or a yellow triangle, your drivers are not installed correctly (refer back to Step 1).
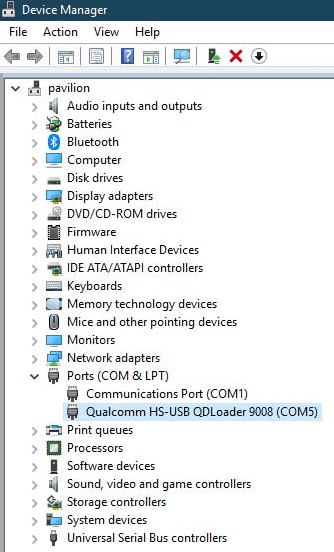
Qualcomm 9008 driver installation in Device Manager
Once the connection is established, the tool will automatically erase the FRP partition. This typically takes less than 15 seconds. You will see a “Success” or “All Done” message.
Step 5: Reboot
Disconnect the phone and power it on. The initial boot may take slightly longer than usual. When the “Welcome” screen appears, you will find that the Google account verification step now has a “Skip” button, allowing you to set up the phone as new.
Risks: Malware, APKs, and Data Safety
Downloading unverified software is the single biggest risk users face when attempting to unlock their devices. When I first researched solutions, search results were cluttered with links to “Magic FRP APKs” hosted on obscure file-sharing sites.
It is critical to understand that many files labeled as an FRP bypass APK often contain malware designed to steal personal data or install adware on your computer. Because the FRP lock Samsung A12 Android 13 no PC process requires a high-level system permissions, granting access to a malicious tool can compromise your entire system.
Safety Verification Checklist
Before downloading any tool (even the one recommended above), run it through this safety check to protect your data:
- Source Credibility: Only download from reputable technical forums (like XDA Developers) or the official SamFw website. Avoid generic “APK download” aggregator sites.
- VirusTotal Scan: Always upload the executable file to VirusTotal.com before opening it. If more than 2-3 generic vendors flag it, proceed with extreme caution or delete it.
- HTTPS Encryption: Ensure the download site uses a secure HTTPS connection.
- File Extension: Be wary of files that end in
.exeif they claim to be an Android app (which should be.apk).
Troubleshooting: Model Variants (A12 vs. Nacho)
Identifying the exact model number of your device is a mandatory step before attempting any bypass procedure. The Samsung Galaxy A12 was released in two distinct hardware variations that look identical on the outside but function differently internally.
- Samsung Galaxy A12 (Standard): Model SM-A125F/M/G. Runs on MediaTek Helio P35.
- Samsung Galaxy A12 Nacho: Model SM-A127F/M. Runs on Exynos 850.
Why The Chipset Matters
The method described above uses the MediaTek BROM exploit. This works only on the SM-A125. If you attempt to use an MTK tool on the Exynos version (A12 Nacho / SM-A127), the software will fail to connect because the Exynos chip does not have a BROM mode accessible in the same way. It may simply throw a “Connection Failed” error. Since the Exynos chipset lacks the BROM exploit, you won’t be able to use this tool; instead, you’ll need to rely on standard Android 13 FRP bypass techniques to unlock the Nacho variant.
How to Verify Your Model
To confirm your model without accessing the settings menu, enter Recovery Mode:
- Power off the phone.
- Connect it to a PC via USB.
- Hold Volume Up and Power simultaneously until the Samsung logo appears, then release Power but keep holding Volume Up.
- On the recovery screen (black screen with yellow/blue text), look at the top line. It will display the model number: SM-A125F (MediaTek) or SM-A127F (Exynos). Ensure your selected method matches this code exactly.
Frequently Asked Questions (FRP & Legality)
Does any ‘no PC, no SIM’ method still work on my Galaxy A12 in 2026?
If your device is running Android 12 or 13 with security patches from late 2023 onwards, the success rate is extremely low. Samsung has patched the “Accessibility” and “Knox” exploits. The PC-assisted MTK method is currently the standard for updated devices.
I followed the steps, but the tool says “Waiting for device” forever. Why?
This is almost always a driver issue. Specifically, Windows has likely blocked the “MediaTek Preloader” driver because it is unsigned. You must restart your PC and disable Driver Signature Enforcement (see Step 1 above), then reinstall the drivers. Also, try a different USB cable and port.
Can I use the SP Flash Tool instead of SamFw?
Yes, you can use the SP Flash Tool, but it is more complex. You will need to manually locate the specific “Scatter File” for the SM-A125F and a separate “Auth Bypass” utility (like MCT MTK Bypass) to disable the boot protection before SP Flash Tool can write to the device. We recommended the all-in-one tool above to simplify these steps.
Is bypassing FRP legal?
Bypassing FRP is generally considered legal if you are the legitimate owner of the device and have simply forgotten your credentials. However, modifying a device that you do not own, or one that has been reported lost or stolen, is illegal. This guide is intended solely for educational purposes and for owners restoring access to their own property.
What should I do if the method fails after a security update?
If a specific tool fails after a new firmware update, do not attempt to force the process with incompatible files. You may need to wait for the tool developers to update their software to support the new security patch binary.
Conclusion: Regaining Access to Your A12
Getting stuck on the Google verification screen after a reset is a frustrating experience, especially when popular Samsung A12 FRP bypass without PC or SIM tutorials result in frustration. While the appeal of a manual, computer-free fix is understandable, the security updates on Android 12 and 13 have largely made these methods obsolete for the MediaTek A12.
By identifying your specific model (SM-A125F), disabling driver enforcement on your PC, and using the automated SamFw MTK solution, you can bypass the lock safely. This method avoids the risks of shady APK downloads and saves you hours of failed manual attempts. Verify your model number, install the drivers correctly, and restore your device to a usable state today.
